Will YOUR Organization survive the Cloud Transformation?
-
Strategic
Imperatives -
Growth
Gap -
The Yellow Brick
Road -
Transformational
Growth
Strategic Imperatives For Cloud
Enterprises without a robust hybrid, multi-cloud strategy will struggle to serve clients and offer new services amid rising competitive intensity.
Demand for hyperconnected “edge-to-cloud” environments and disruptive technologies will increase the complexity of the global cloud ecosystem.
Integrated, future-focused artificial intelligence (AI) strategies customized for different industries will push cloud service providers ahead in the race for AI supremacy.
How do you shift from where you are to what you want to become? How do you fill the gap?
Based on those strategic imperatives the gap between where you are now and where you need to be to achieve transformational growth is daunting.

Effective Growth Coaching increases productivity by over 53%

Over 40% of professionals would like to have more meaningful networks

84% of Executives say Innovation is critical but lack resources
The Three Components Required for Transformational Growth
Growth Opportunities for Cloud

Industry Clouds
Developing customized, industry-specific cloud solutions to drive new customer acquisition and retention.
Integrated Services
Focusing on flexible platforms and API-based integration tools to develop a suite of value-added, advisory, and management services for enterprises while building future-forward revenue pipelines.

Cloud cost and resource management software platforms
Creating integrated management tools that offer complete visibility and intelligent insights across multi-cloud configurations, on-premises infrastructure, and SaaS services to optimize enterprise performance.

Data-specific Clouds
Offering a suite of services that integrate advanced AI analytics for data migration, management, and replication, to help clients tame their data, while capitalizing on new business models.
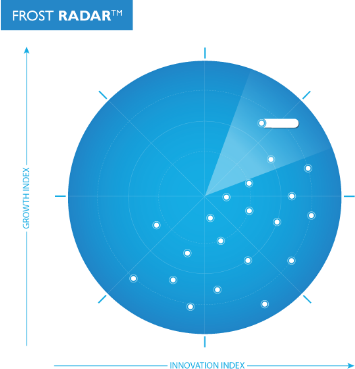
Frost RadarTM
Benchmarking Your Future Growth Potential
Our work is focused exclusively on identifying the growth opportunities of the future and evaluating companies that are best positioned to take advantage of them. The Frost Radar™ is a robust analytical tool that allows us to evaluate companies across two key indices: their focus on continuous innovation and their ability to translate their innovations into consistent growth.
To discover how you benchmark
against competition
A PRACTICAL, HIGH IMPACT, SCALABLE TRACKING SOLUTION
Measure with The Growth
& Innovation Index
-
2
Major Indices
-
10
Analytical Algorithms
-
1
Platform
Recognizing Excellence and Leadership in Information and Communications Technology for 20 years
Our best practices analysis provides in-depth examination of successful strategies and tactics used by leading companies across all industries, and offers recommendations for implementation to drive performance and success
2022 Technology Innovation Leadership Award- Disaster Recovery as a Service, Global
Read More2022 Company of the Year Award- Digital Employee Experience Platform, North America
Read More2022 Competitive Strategy Leadership Award- Hybrid Cloud Management Platform, Global
Read More2021 Technology Leadership Award- Managed Enterprise Resource Planning (ERP) Enabling Technology, Global
Read MoreExperience
Analysts
Connect with the Brightest Minds in Growth Innovation Leadership
Our community activates your success with our peer-to-peer network, peer meetings, annual growth events, executive roundtables, and access to inspiring activities such as our innovation workshops.
Join our exclusive community of like-minded professionals today.
Join Growth CommunityGrowth Council Think Tank Series

How The Hybrid Cloud Supports Remote Work

Why The C-Suite Should Pay Attention To Cloud Governance

How Can Organizations Leverage The Cloud To Manage Innovation

Is A Poor Multi-Cloud Strategy Limiting Your Business Growth?

Is Your Cloud Strategy Delivering Your ROI Objectives?

Mastering The Complexity Of The Cloud Ecosystem

Can You Trust Your Healthcare Cloud Set-Up?

Are Your Employees Digitally Literate Enough To Deliver Success?

Leveraging Cloud To Deliver Your Digital Transformation Goals

Is Your Technology Hindering Employee Satisfaction & Productivity?

Pay-Per-Use Vs. Subscription - Which Model Works Best For Your Business?
Activate your transformational journey
Through growth coaching you will gain the tools necessary to develop powerful growth pipeline strategies that will fuel the future of your company.
Growth Coaches | Think Tanks | Growth Experts
Growth for Leaders & Companies
Maximized through collaboration
Continuous flow of Growth Opportunities
Proven Best Practices
Optimised Customer Experience
Implementation Excellence
Industry Leadership
"*" indicates required fields

How to Transform Your Business with Future-proof Cloud Strategies?

From Missed Opportunities to Action: Bridging the Growth Gap with the Power of Hybrid and Multi Cloud Ecosystems

Companies to Action: Accelerating Digital Transformation with Disruptive Cloud Technologies
How to Transform Your Business with Future-proof Cloud Strategies?
Navigating Complex Cloud Ecosystems on the Path to Digital Transformation
The proliferation of disruptive cloud technologies is revolutionizing businesses as organizations flock towards cost-effectiveness, flexibility, and agility in the race to streamline operations and scale infrastructure in an interconnected, digital world. As the foundational pillars of digitalization, technologies like artificial intelligence (AI), machine learning (ML), internet of things (IoT), blockchain, and edge computing, necessitate robust and future-ready cloud ecosystems, to help businesses drive positive results. Are your teams ready to track, identify, and implement emerging technologies to thrive through this transformation?
Now, organizations are rejecting the “all-in” public cloud strategy and embracing hybrid and multi-cloud models instead. This unlocks the convenience and benefits of centrally managing workloads across their IT tech stacks. Furthermore, the ease of developing and delivering cloud-based applications (through Software-as-a-Service) is heightening competitive intensity in an industry where start-ups and established software firms are being pushed to maximize value creation for subscribers that aren’t bound by loyalty or term contracts – against this backdrop, does you company have the right strategies to optimize cloud innovation and align internal teams? Or is your business struggling to leverage the potential of cloud to your advantage?
Overcoming Growth Barriers in Cloud
Hybrid and multi-cloud models offer unparalleled opportunities for organizations to transform their operations and unlock new levels of agility and competitiveness. However, executing and implementing the right cloud strategies comes along with a myriad of challenges like the complexity of data migration, maintaining data integrity, establishing regulatory compliance, and identifying best-fit infrastructure. Moreover, the intricacy of hyperconnected ‘edge-to-cloud’ ecosystems, the need for AI-driven capabilities, and multi-faceted integrations with vendors, service providers, and legacy infrastructure makes optimizing cloud environments increasingly difficult. Now, whether you emerge as a victor or victim of this cloud transformation depends on how your teams adapt and leverage the opportunities it presents.
- Which business models are driving the cloud transformation and how best can your teams leverage these to overcome growth barriers?
- How will you capitalize on automation to integrate advanced intelligence in your existing platforms?
- How can your teams ensure seamless migration of data/ applications across legacy and new cloud infrastructure?
While the cloud transformation brings along the potential of optimal resource utilization for businesses through “pay-as-you-go” models, organizations face the additional task of carefully managing and monitoring network and infrastructure expenses. Cloud resource optimization, monitoring and governance, and the utilization of efficiency enhancement tools are crucial to capitalize on new growth opportunities in cloud- What tools will you use to evaluate the ROI on your cloud investments and which growth opportunities will empower your teams to create recurring revenue pipelines?
Embracing Hybrid, Multi-cloud Strategies to Maximize Flexibility in IT Infrastructure
As the global demand for cloud services continues to escalate, cloud providers, technology vendors, and service providers face the imperative to evolve with agility to meet and exceed evolving customer needs. Tomorrow’s enterprises require more than just basic infrastructure and storage capabilities; they seek comprehensive, customized solutions that align with specific business needs and empower them to drive innovation, enhance operational efficiency, and achieve strategic growth goals. To meet these evolving demands, providers are being pushed to adapt their offerings, enhance their service capabilities, and establish collaborative approaches to accelerate innovation.
- Do you have a growth pipeline management framework to identify the latest opportunities in industry cloud, integrated services, resource management, and edge-2-cloud?
- Which strategic partnerships and collaborations will help you differentiate your solution portfolios?
Are You Ready to Evaluate Your Cloud Alignment and Transform Your Business?
To navigate evolving business ecosystems, companies across the ICT continuum must identify and overcome crucial growth barriers. The key to success is prioritizing the right opportunities that align with your growth vision and implementing the best-fit strategies. Frost & Sullivan has six decades of experience in connecting global mega trends, emerging technologies, and new business models to drive radical growth. We help companies identify, evaluate, and prioritize best-fit opportunities that empower them to thrive through change.
Let us guide you through your transformation journey by working collaboratively with the ecosystem community of companies in the Cloud continuum. This journey is fuelled by four powerful components, ensuring your success in navigating industry changes:
- Schedule a Growth Dialog with our team to dive deeper into transformational strategies and explore specific needs within your company.
- Become a Frost Growth Expert in your area of specialization and share your expertise and passion with the community through our Think Tanks.
- Join Frost & Sullivan’s Growth Council and gain access to think tanks focused on transformational growth strategies leveraging advancements in Cloud.
- Designate your company as a Company to Action to increase exposure to investors, new M&A opportunities, and other growth prospects for your business.
From Missed Opportunities to Action: Bridging the Growth Gap with the Power of Hybrid and Multi Cloud Ecosystems
Cloud Acceleration: An Essential Step Towards Digitalization
The rapidly expanding global cloud ecosystem is creating new opportunities for organizations to hone their existing cloud deployments and transcend the limitations of conventional workload management, inadequate flexibility, restricted visibility, latency, and rigid architectures. As the pressure to optimize rising cloud costs and mitigate the risk of service disruptions intensifies, global businesses are increasing their reliance on hybrid and multi cloud models to introduce the benefits of distributed architecture in their customer value chains. Adding to this complexity, the accelerated pace of digitalization and technical innovation across industries has organizations grappling to evaluate emerging cloud services and determine whether (or how) to leverage these to their advantage. Now, whether you emerge as a victor or victim of this cloud transformation depends on how your teams leverage the opportunities it presents.
- Which growth processes will empower your enterprise to navigate the intricacies of an evolving cloud value chain?
- Which strategies will help your business ease the seamless orchestration of workloads across public, private, and hybrid cloud models?
Further, the expansion of edge computing and thereby, the expansion of hybrid cloud places new demands on corporate networks, as business try to seamlessly connect multiple cloud data centers with numerous branch and edge locations, middleware, and different layers of their tech stacks. Now, adopting the optimal mix of digital tools in conjugation with innovative cloud solutions will help enterprises derive more value from complex data to improve visibility and analytics. To reap the benefits of cloud computing against this backdrop, businesses are being pushed to embrace flexible and scalable bandwidth that will allow easier access to evolving cloud ecosystems.
- Are your teams ready to assess the impact of disruptive cloud technologies against the growth prospects they ignite?
- How will your organization’s network, endpoints, platforms, and applications need to pivot to realize the full potential of hybrid and multi cloud models?
Bridging the Growth Gap in Cloud Environments
The dynamic landscape of the cloud industry presents an intriguing paradox: while the total addressable market (TAM) for cloud and related services appears vast and promising, there exists a considerable gap between the TAM and serviceable available market (SAM). This disparity stems from a combination of factors like varying technological readiness or maturity of enterprise customers, infrastructure and data framework bottlenecks, budgetary limitations, security and compliance concerns, lack of awareness, and the need for customized cloud solutions. Closing this gap requires concerted efforts, collaboration, and coopetition between the various entities in the cloud ecosystem. This raises pertinent questions for different stakeholders-
- What frameworks will you use to measure hybrid and multi-cloud readiness for different industries?
- How is your organization preparing to surmount implementation barriers in cloud environments to build future-proof revenue pipelines?
- Have you aligned your vision and team to capitalize on the opportunity universe emerging from the growth gap?
By acknowledging the cloud growth gap, identifying the right opportunities, and successfully executing go-to-market strategies, businesses can drive long-term, sustainable growth and establish a robust cloud growth pipeline.
Welcoming the Hybrid Era: Igniting Growth in Multi Cloud Environments
A well-defined, holistic multi-cloud strategy enables enterprises to become more flexible and agile, while simultaneously reducing costs. But having multiple clouds can add to the management burden unless businesses leverage solid platforms to better orchestrate, monitor, and manage workloads. This means that the pressure on providers to enhance functionality, offer flexible pricing models, and deliver open application programming interfaces (APIs) is at an all-time high. As cloud technologies evolve, information and communication technology (ICT) providers and suppliers face the pressure of scaling up to meet evolving customer needs and expectations. This presents unique opportunities for cloud service providers, connectivity vendors, tech giants, and start-ups to redefine their strategies, enhance their offerings, and elevate the level of services they provide.
- Are your teams equipped to establish competitive differentiation through technology-enabled services/ products that maximize customer value?
- How can providers leverage advanced threat intelligence to embed robust security in hybrid or multi-cloud settings?
- Do you have a framework to identify and implement best practices to better serve your customers?
Frost & Sullivan’s Growth Pipeline Engine helps organizations answer these questions and accelerate growth by eliminating strategic distractions. Our unique framework connects five integral phases of business development into a continuous loop—from opportunity evaluation, go-to-market strategies, planning and implementation to monitoring and optimization. We help you pinpoint your growth zone by weighting the global Cloud landscape against your vision to:
- Identify Growth Opportunities fuelled by six unique perspectives.
- Recognize Best Practices, identify disrupters, and implement innovative growth strategies.
- Prioritize Companies2Action to find potential strategic partners that shape the future of Cloud.
Cloud Acceleration: From Aspiration to Achievement
To navigate evolving business ecosystems, companies across the ICT continuum must identify and overcome crucial growth barriers. The key to success is prioritizing the right opportunities that align with your growth vision and implementing the best-fit strategies. Frost & Sullivan has six decades of experience in connecting global mega trends, emerging technologies, and new business models to drive radical growth. We help companies identify, evaluate, and prioritize best-fit opportunities that empower them to thrive through change.
Let us guide you through your transformation journey by working collaboratively with the ecosystem community of companies in the Cloud continuum. This journey is fuelled by four powerful components, ensuring your success in navigating industry changes:
- Schedule a Growth Dialog with our team to dive deeper into transformational strategies and explore specific needs within your company.
- Become a Frost Growth Expert in your area of specialization and share your expertise and passion with the community through our Think Tanks.
- Join Frost & Sullivan’s Growth Council and gain access to think tanks focused on transformational growth strategies leveraging advancements in Cloud.
- Designate your company as a Company to Action to increase exposure to investors, new M&A opportunities, and other growth prospects for your business.
Companies to Action: Accelerating Digital Transformation with Disruptive Cloud Technologies
How Are Leading Cloud Providers Catalyzing Innovation in Cloud Security, Infrastructure, Platforms, and Services?
In the race towards digital transformation, businesses are increasingly turning to the cloud to foster agility, maximize digital resilience, augment customer service management, and increase productivity. Now, spurred by developments in artificial intelligence (AI), machine learning (ML), quantum computing, and 5G, public cloud providers are poised to hasten the pace of AI adoption among enterprise customers, while facilitating hyper-automation. But to succeed, they must first address enterprise challenges in executing their digital transformation, including insufficient expertise, increasing budget constraints, and uncertain return on investment (ROI). This is intensifying the pressure on providers to deliver innovative and cost-effective foundational models, user-friendly toolsets, integrated platforms, and sophisticated edge-to-cloud configurations that facilitate hybrid- and multi-cloud workloads.
- Do your teams have the right set of frameworks to capitalize on the benefits of innovative cloud models?
- How will your growth strategists leverage new technologies to mitigate the complexities of cloud deployment, orchestration, and app modernization?
As the ICT industry evolves, business models are shifting towards end-to-end managed services, driving the demand for holistic solutions that combine cloud, network, and security functionality under service level agreements. Since such solutions involve multiple technology/service suppliers across the enterprise tech stack, hyperscale infrastructure-as-a-service (IaaS) providers are being challenged to develop lucrative partner programs, that benefit all parties of the cloud ecosystem.
- Which business models will help your leadership team to better align your current cloud solutions/services portfolio with evolving customer needs?
Facilitating Digital Transformation: Leading Providers that are Putting Future-proof Cloud Strategies into Action
The following pioneers in cloud solutions and services are driving growth and innovation to meet evolving customer demands. They play a crucial role in simplifying cloud orchestration and cybersecurity management, empowering organizations to optimize business processes and harness disruptive technologies. Leveraging systematic portfolio expansions, strategic innovation, and calculated growth strategies, these firms are delivering easy, efficient, and consistent management of diverse digital/physical infrastructure:
Do You Have What It Takes to Become a Trailblazer in the Evolving Cloud Ecosystem?
As businesses advance on their digital transformation journey, they increasingly aim to automate repetitive tasks like handling infrastructure and functions further along the technology stack, such as data management, cost optimization, security initiatives, and network orchestration. Now, in a landscape of dynamic/distributed architectures involving multiple workloads, technologies, and services, “Companies to Action” in the cloud ecosystem exhibit strategic vision and innovation, delivering cutting-edge technologies and holistic solutions to meet evolving customer needs with compelling go-to-market strategies and new business models.
- Which growth initiatives and partnership strategies will help your teams channel cloud innovation to maximize competitive differentiation?
About Frost & Sullivan
Frost & Sullivan, the growth pipeline company, enables clients to accelerate growth and achieve best-in-class industry positioning in terms of innovation and leadership. The company’s ‘Growth Pipeline-as-a-Service’ provides corporate management teams with transformational strategies and best-practice models that catalyze growth opportunity generation, evaluation, and implementation. Let us coach you on your transformational journey, while we actively support you in fostering collaborative initiatives within the global cloud ecosystem. This journey is fueled by four powerful components, ensuring your success in navigating dynamic business and industry landscapes.
- Schedule a Growth Dialog with our team to dive deeper into transformational strategies and explore specific needs within your company.
- Become a Frost Growth Expert in your area of specialization and share your expertise and passion with the community through our think tanks.
- Join Frost & Sullivan’s Growth Council and become an integral member of a dynamic community focused on identifying growth opportunities and addressing critical challenges that influence industries.
- Designate your company as a Companies to Action to maximize your exposure to investors, new M&A opportunities, and other growth prospects.













