In the past few years, the business benefits of edge computing have become more apparent. As a result, edge computing is growing rapidly in the industrial and commercial sectors. There are a plethora of use cases for edge: oil operators can benefit from faster access to data to mitigate disasters during critical failure, enterprises can enhance video surveillance, marketers can push special offers to customers, and the healthcare sector can create a vastly superior patient monitoring system. The underlying primary benefit, however, for all users is the ability to lower the burgeoning IT expenditure on cloud and network bandwidth costs. As data volumes mount and the desire to store every data point becomes harder to justify, there is a strong operational implication for edge computing. Besides costs, local processing of high-volume data could provide faster analytics to manage local devices and maintain high-quality business services when a few seconds can make all the difference—such as in the event of a critical equipment failure in a factory or a rig site.
As operations become more geographically distributed, IT operations teams are increasingly inundated with data from several thousand on-premise data centers and cloud infrastructure components. However, the truth remains that only an estimated 1% of the monitoring data is useful to derive business insights, such as anomaly detection or predictions of forthcoming events. With local processing and insight generation, edge computing can prevent transmission of terabytes of irrelevant data to the cloud or data centers and send only the relevant, actionable data that generally is a tiny sliver of the actual data.
Burgeoning landscape for applications at the industrial edge
In industrial applications, there is broad industry consensus on the need and value of the edge, despite the uncertainty around how the move toward the last-mile of distributed networks will unfold, especially in the enterprise, alongside the influx of IoT and other private networks. New and innovative use cases are emerging every day in conjunction with edge technology. AI (Artificial Intelligence), in particular, has emerged as a key leading-edge use case that is slated to bring significant value to enterprises. AI, augmented reality (AR), virtual reality (VR) and mixed reality are being adopted in discrete manufacturing, process industries, retail, utilities, automotive and construction. AI and AR/MR adoption needs a highly flexible, scalable, responsive compute infrastructure with 24/7 availability. Edge has emerged as the panacea to deliver a low-latency experience, services and instances of the applications closest to the end users.
The dawn of IoT and its networking potential began almost a decade ago, but organizations still face various roadblocks on the way to full-scale adoption. Potential IoT network issues can also create challenges with edge computing, the underlying architecture that supports IoT and processes data closer to the source. But many IT decision-makers still view edge computing as a potential threat to their organization due to security and adoption risks.
Key challenges of adopting edge computing
Most IT decision-makers recognize the enhanced business and network efficiency of IoT devices. However, the majority of IoT projects don’t pass the proof-of-concept stages due to various challenges. Broadly, these challenges can be categorized into standards, infrastructure, security and frameworks.
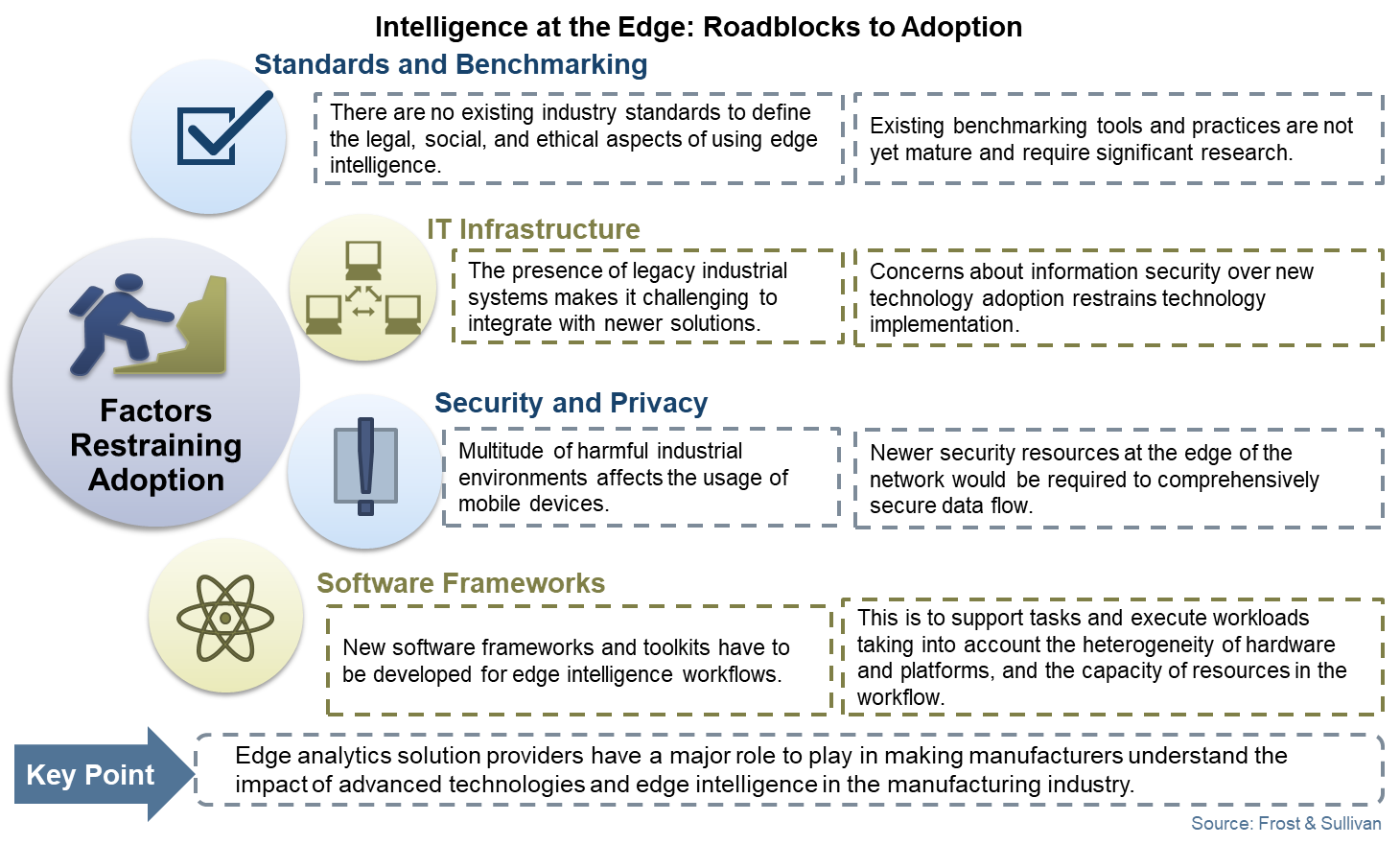
Edge-specific security threats are still not fully understood: Edge devices are generally small, cheap and not designed with security in mind. For ease of use, a majority of these devices don’t mandate any authentication with third-party APIs. To save costs and speed up deployment, a lot of them don’t encrypt data natively. Edge devices often become the weakest link in the event of a cyberattack. This security risk is a key concern for IT and network managers. There is a growing number of edge devices that are already collecting personally identifiable information, such as email, phone numbers, health data or financial formation, including credit card data for customers and staff. Most IT managers need a security framework in place before the large-scale roll-out of edge projects.
New environments call for new rules of management: The majority of IT managers believe that a lack of universal rules and regulations for device management is another challenge for edge computing and IoT network architecture. In recent years, the U.S. and U.K. governments have developed IoT standards and regulations, and many IT managers are still working on understanding the local implication of these regulations in their respective organizations.
The lack of a single, centralized OS specifically for IoT networks that organizations can safely rely upon is a key hindrance to growth of centralized IoT networks. Due to the absence of central consistent, reliable security and updates, processes cannot be guaranteed. Organizations ready to move more data and application assets to edge computing environments are still holding back their decisions due to the need for a framework of new policies and thresholds for central processing and alerting of all that data.
Another framework challenge is the uncertainty over how the move to distributed networks will transpire, especially in the enterprise, alongside the rise of IoT and private networks. Enterprise players and service providers are both trying to position themselves to capitalize on the edge. The difference in the framework and approach proposed by both types of players often complicates and impedes decision making among end-users.
Integration in a multi-cloud environment: Integrating edge computing applications and platforms into the existing cloud architecture is vital for realizing the true potential of edge computing. Edge computing is the missing link and the key middle layer between devices (original data source) and cloud computing (core network). The limited storage and compute capability of edge nodes requires a well-performing, co-existing system between edge and cloud. With the growing adoption of multi-cloud environments among enterprises, establishing a redundant edge network to handle the incoming data traffic from multiple nodes will be a challenge for the cloud. Most IT managers are still struggling with finding pliable solutions and cloud vendors that can accommodate the high bandwidth needs, as well as the redundant data reporting and routing requirements.
Heavy initial capital investment: R&D in edge enabled software frameworks and hardware devices must be assisted by substantial capital investment, which will certainly raise the initial costs of edge computing. This investment is required to support tasks and execute workloads, taking into account the heterogeneity of hardware and platforms and the capacity of resources in the workflow due to the introduction of edge. The initial capital required for availing the necessary infrastructure, as well as expertise, is even higher in emerging economies due to weak connectivity and network provisions. Investment in edge often finds itself competing with other investment priorities in enterprises.
Lack of awareness amongst SMEs and government sectors: More than a third of IT managers and decision-makers are still not fully aware of the scope and end uses of edge computing. Some of the developing countries in the Asia-Pacific are still becoming familiar with cloud computing as a technology, and the adoption of edge computing functionalities will require a considerable amount of time. Many service providers in APAC and other emerging economies are still using micro data centers as a backup to their core data center facilities rather than for edge workloads.
Edge monitoring tools are still a work in progress: Before the IT managers deploy edge computing and open a floodgate of new devices in their network, they need assurance that there will be a smart performance monitoring platform in place that will monitor every issue faced by remote applications and Microservices. After the major roll-out of 5G, billions of devices will be communicating machine-to-machine, and the addition or subtraction of connected devices will be possible at an unprecedented scale. Without a monitoring platform for the edge, the reliability of edge will always remain questionable for IT managers and, hence, dissuade adoption.
The IT operations team is at a crossroads of making major decisions about their evolving network architecture and adapting to a more distributed and hybrid cloud world. This new architecture would invariably have edge computing as a fundamental element of their digital strategy. Rapid innovations in edge security, governance, standards and framework are the only way to alleviate adoption challenges and unleash the benefits of edge computing.



